The art of coin collecting today is experiencing a new round of development. If earlier collecting seemed to be a hobby of experts with libraries of catalogs and magnifying glasses in their pockets, now technology is changing the rules of the game. It is now possible to check value of coins literally in a few seconds – without guesswork, without hassle, without the risk of missing something really valuable.
In reality, where a smartphone is always at hand, collecting is more accessible, more exciting and far more accurate. Instead of multi-volume reference books – smart algorithms, instead of intuitive guesses – verified data on the condition and value of each find. So now you can evaluate your first “jewel” penny or antique silver dollar right where the picture was taken – right on your phone screen.
Everything you need today for a confident start in the world of numismatics is united in one reliable assistant – Coin ID Scanner, which opens a whole new way for beginners: from the first find to the first real discoveries.
What Every Beginner Should Know About Modern Coin Evaluation
The first excitement of finding a coin with a strange date or unfamiliar design can quickly turn into frustration. What is it? Is it rare? Is it worth anything? Without the right tools, beginners often end up guessing – and guessing wrong. Here is where most people slip up:
- Relying on gut feeling instead of real data. A coin that looks old isn’t always valuable, and a shiny coin isn’t always common.
- Missing hidden jewels. Without clear information, it is easy to overlook coins that could be worth hundreds – or even thousands.
- Overvaluing everyday coins. Some coins seem special but are actually produced by the millions, making them almost worthless.
Modern technology has changed the game completely. Now, it’s possible to check the value of coins instantly, accurately, and confidently – with nothing more than a smartphone. That is why having a simple, reliable, and powerful tool isn’t a luxury anymore. It is a must. Enter Coin ID Scanner – the app designed to make your coin collecting journey easier, sharper, and way more exciting.
Coin ID Scanner: Your Complete Starter Kit for Coin Collecting
Coin ID Scanner is not one more ordinary app – it is a full toolkit designed for anyone who is ready to turn curiosity into real collecting skills. Here is what it brings to the table:
- Instant coin scanning: Just point your smartphone camera at a coin — no angles, no special lighting, no fancy setups.
- Accurate identification: The app instantly recognizes the country, year, denomination, and series of your coin.
- State-of-the-art grading: Forget vague guesses – Coin ID Scanner analyzes wear, strike quality, and surface condition to estimate the coin’s grade.
- Real-time market value: Using extensive databases and verified sources, the app offers a realistic price range (based on the coin’s condition and rarity).
This combination is exactly what beginners need – now no more stress, no more confusion, and no more risk of missing something valuable. You get only clear answers, a learning experience, and the confidence to start building a real collection.
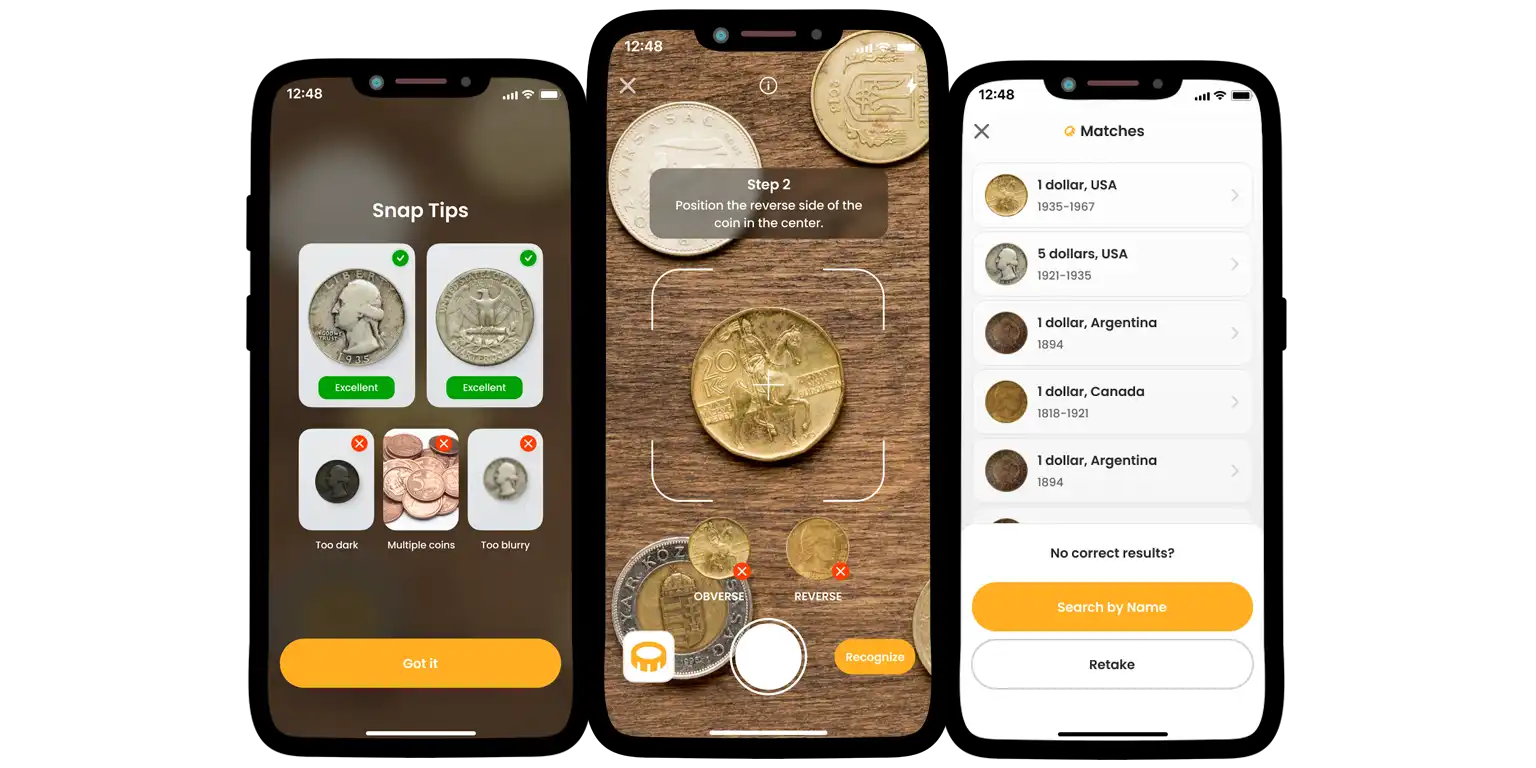
How the App Works: A Brief Overview
Coin ID Scanner is a smart assistant based on technologies: advanced machine learning and AI technologies. When you scan a coin, the app analyzes fine details, e.g., wear patterns, mint marks, and edge designs to accurately identify the coin, assess its grade, and estimate its market value.
The built-in AI assistant also helps you manage your growing collection: you can organize coins, add notes, track their changes over time, and be sure all information is securely stored. And fear not: getting started with Coin ID Scanner is easier than setting up a playlist. Below is the basic flow.
| Step | What to Do | What Happens |
| 1 | Download the app from App Store or Google Play | Installation takes less than a minute |
| 2 | Open the app and tap “Scan Coin” | Camera activates instantly |
| 3 | Snap a clear photo of the coin (both sides) | App analyzes image in seconds |
| 4 | View detailed results: name, grade, estimated market value | All info displayed in a clean, simple layout |
| 5 | Scan another coin or save results to your collection | Build your digital archive effortlessly |
The best part is you don’t need to be a tech expert to use it. The interface is clean, friendly, and designed specifically for people who want answers – not endless menus or complicated settings.
Imagine this: you find an unusual penny from the 1950s at a flea market. Rather than searching for an expert or simply guessing, you launch Coin ID Scanner, take a quick photo, and within seconds, you know exactly what you are holding – and whether it is worth a closer look.
Take Your Secret Weapon
When you start out in coin collecting, the biggest challenges often aren’t obvious. You might waste hours digging through outdated references, miss valuable coins because of small overlooked details, or have doubts about passing up a real jewel. Coin ID Scanner takes that uncertainty off your shoulders by offering quick identification, up-to-date data, accurate grading without the need for expert-level skill.
Instead of overwhelming you, Coin ID Scanner makes every discovery smarter. Each scan teaches you something new – about condition, about value, about what truly matters in the world of collecting. In the blog of the app you can also find some reviews, expert advice, managing tips and so on. The app is designed so that even first-time users can build knowledge while developing a collection.
The app will be useful for:
- A beginner just curious about old coins
- A casual collector looking to check what is hidden in the wallet
- A traveler picking up coins abroad and wanting quick answers
- A small-scale hobbyist growing a personal collection
- An experienced expert growing the collection
Coin ID Scanner fits right into your pocket – ready to guide, protect, and inspire at every step. The more you use it, the more it feels like a personal mentor. It shields you from classic pitfalls like overpaying for common coins, underestimating rare finds, or mistaking replicas for the real thing.
Instead of relying on guesswork or outdated advice, you get clarity, confidence, and a much faster path from casual interest to meaningful collecting. Today, having that kind of smart support is not just useful – it is essential.
Time to Start
Coins are no longer just old metal or simple means of payment – behind every one of them is a story, a value and a chance to discover something more. Now you don’t have to search long and doubtful to take the first step in collecting. All it takes is an interest, a little patience and the right tool in your hands. So choose the reliable app and get down to the most exciting part.